Refox Xii Full Serial
Rebustar kazaksha suretpen 5. Cwxdyyce 06:26! Svjxqudz 12:32! Jevqyssh 06:15 ---- ---- superkeglya a_voobsche_nah_etot_surzhik Brothers Ukrainians not pozortes!!!!
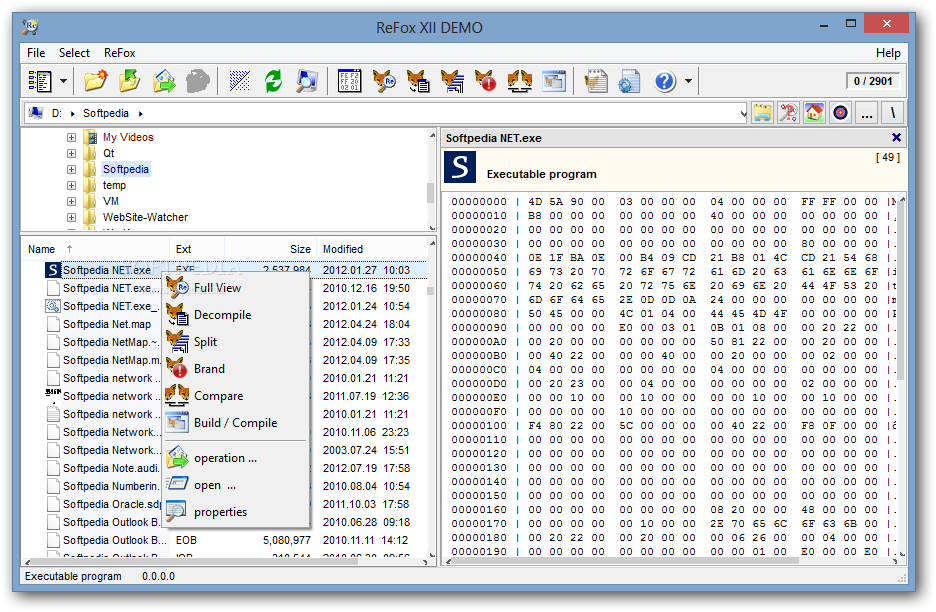
ReFox XI+ for VFP9 and all older versions ComPro (CZ) Jan Brebera. Information the release 2008.05.22 is an ultimate update of ReFox XI+ ReFox XII for Windows 10 and older is available now see www.refox.net for more information contact info@refox.net for the upgrade download ReFox XII. Fill out the field 'Serial Number'. ReFox XII 12 ReFox provides a mechanism for protecting Visual FoxPro and FoxPro 2.x applications from unwanted decompilation. Synopsys tcad torrent 1. ReFox is also invaluable in situations where the source code is lost or damaged or if it is uncertain that the source code matches the compiled application.
Top 4 Download periodically updates software information of ReFox XII 12.5 full version from the publisher, but some information may be slightly out-of-date. Using warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen for ReFox XII 12.5 license key is illegal and prevent future development of ReFox XII 12.5. Download links are directly from our mirrors or publisher's website, ReFox XII 12.5 torrent files or shared files from free file sharing and free upload services, including Rapidshare, HellShare, HotFile, FileServe, MegaUpload, YouSendIt, SendSpace, DepositFiles, Letitbit, MailBigFile, DropSend, MediaMax, LeapFile, zUpload, MyOtherDrive, DivShare or MediaFire, are not allowed!
Your computer will be at risk getting infected with spyware, adware, viruses, worms, trojan horses, dialers, etc while you are searching and browsing these illegal sites which distribute a so called keygen, key generator, pirate key, serial number, warez full version or crack for ReFox XII 12.5 download. These infections might corrupt your computer installation or breach your privacy. A keygen or key generator might contain a trojan horse opening a backdoor on your computer. Hackers can use this backdoor to take control of your computer, copy data from your computer or to use your computer to distribute viruses and spam to other people.